The effect of Information Technology on the Audit
In today’s world, everything is developing rapidly and has great effects on our lives, of course, every good technology adds value to our lives, but creates certain results depending on how it is used. In other words, in the simplest terms, a match can light your stove and allow you to sit at a happy family table in the evening, while it can light a forest in the hands of an ill-intentioned person.
In the modern business world, it is an inevitable fact that many factors such as business volumes, complexity, location differences, and the importance of fast and accurate information cause errors and fraud. Putting aside making money and achieving our desires, I think we need to be more careful in order to maintain/protect a value in which we spend at least 8 hours of our daily life. Technologically, many software have helped the companies and entities and facilitated the work of entities. But even the best systems do not avoid the share of errors and fraud.
International Standard on Auditing requires the auditor to understand the entity and its environment, including the entity’s internal control in order to assess the risks of material misstatement in the financial statements. In planning the portions of audit which may be affected by the client’s environment the auditor should obtain an understanding of significance and complexity of computerized information system activities and the availability of data for use in the audit.
An auditor can use manual audit procedures (called auditing around the computer) and computer assisted audit techniques (CAATs, called auditing through computer) or a combination of both. However, in both cases, the reliability of systems is highly contingent upon the adequacy of control, design and implementation, and it is crucial for the Auditor to understand the structure and use of the control system through inquiry and observation.
Auditing around the computer; it is known as black box audit approach, auditors can use to evaluate client’s computer system by picking source documents at random and verifying the corresponding outputs with the inputs. In simple terms, auditor compares the independently determined results to the program results, regardless of how the inputs are processed to provide the output. That’s why, the auditor does not directly test the application program. Sometimes it also means conducting audit without the use of computer system. Auditing around the computer is only suitable for simple batch systems with a good audit trail. The advantage of this strategy for testing controls is that there is no need to test the complexities of computer programs due to auditor is already aware of the software’s reliability or auditor has no mean to gain understanding of the computer system such the below reasons;
- lack of appropriate system documentation
- auditor lacks expertise or skills to understand/use the computer system for auditing purposes.
- auditor is not given access to computer system at the level required
As a disadvantage, risks of auditing around the computer include insufficient, paper-based evidence and insufficient audit procedures.
Auditing through the computer; is an audit approach used in more complex IT environments where internal controls are embedded in applications that are visible only in electronic form. Computerized audit techniques range from procedures as simple as listing the data in a given file to the use of Artificial Intelligence tools to predict financial misstatements or financial statement structures. Auditing through the computer describes the various steps taken by auditors to evaluate client’s software and hardware to determine the reliability of operations. The five techniques called Computer assisted audit techniques (CAATs) such as “Transaction Tags”, “Embedded Audit Modules”, “Test Data”, “Integrated Test Facility, “ Parallel Simulation” used in auditing through the computer to validate programs.
Computer assisted audit techniques (CAATs) refer to the use of technology to help you evaluate controls by extracting and examining relevant data. Sophisticated use of CAATs can be known as ‘data analytics’ and is increasingly being used across the profession.
- Transaction Tagging; It is a technique the auditor uses to electronically mark (or tag) specific transactions and follow them through the client’s system.
- Embedded Audit Modules; embedded audit modules are usually built into the application program when the program is developed. The insertion of an audit module into the client’s application system to capture certain transactions. Besides its many benefits such as continuous monitoring, identifying actual transactions and other info that meet criteria having significance, On the other hand, the auditor may experience extra overhead in using extra programs to install into the company’s software.
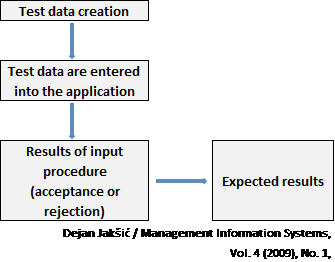
- Test Data; It is a technique that uses the application program to process a set of test data, the results of which are already known. The processing of the auditor’s test data through the client’s computer system using the client’s application program to determine whether the controls embedded in the computer accurately process the test data. The client’s system is used to process the auditor’s data, off-line, while still under the auditor’s control.
The auditor compares the output generated by the system with the expected output in order to evaluate the effectiveness of the program’s controls.
- Test data (with a predetermined result) are processed by the client’s computer programs under the auditor’s control.
- The test data need consist of those valid and invalid conditions that interest the auditor.
- Only one transaction of each type need be tested, as the system should process similar transactions in a consistent manner.
Test data consist of correct and incorrect data. If incorrect data is entered into the system, auditor expects the input rejection.
- Integrated Test Facility; Integrated test facility runs test transactions through “live” system and posts to simulated (dummy) files to provide an audit with information about the operating effectiveness of controls. Integrated test facility is similar to the test data approach, except that the test data is commingled with live data. The client’s system is used to process the auditor’s data, online.
This approach is used primarily with large-scale, online systems serving multiple locations within the company or organization. Integrated test facility is a variation of test data technique. The main difference is that instead of checking information system while not in use, simulated data are added to client’s real data and processed simultaneously.
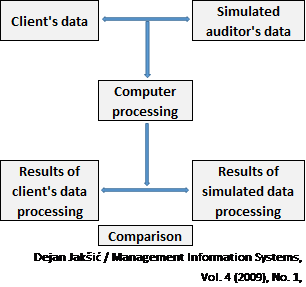
In order to avoid contamination of client’s real data, procedures for separation and extraction of simulated data from the computer system should be defined before the application of integrated test facility technique and executed upon the end of testing.
- Parallel Simulation; It is a technique in which the auditor reprocesses some or all of the client’s live data by using the auditor’s own software and the data used in the auditor’s software should be the same data used by the client. The output from the client’s software is compared with the output from the auditor’s software. Differences in output may indicate weaknesses in internal control.
Generalized Audit Software (GAS);
GAS is a tool used by auditors to automate various audit tasks. It helps auditors to analyze data electronically where it is quite impossible to do so manually. Generalized Audit Software (GAS) is a class of CAATs that allows auditors to undertake data extraction, querying, manipulation, summarization and analytical tasks. GAS is stated to be the most influential Computer assisted audit techniques (CAATs) that can facilitate the audit objective. Software such as the Audit Command Language (ACL), Interactive Data Extraction and Analysis (IDEA) and PanAudit Plus (and so on) run in a PC environment and enable Auditors to interrogate mainframe and networked applications throughout the firm’s local area network.
Although there is not enough interest among auditors today, there is no doubt that using data analyst software, which is artificial intelligence products, will increase reasonable assurance on audit quality and accuracy of financial statements. For those who are curious and want to learn more, I recommend you to read two useful studies the below;
- Employing Generalized audit software in the financial Services Sector: Challenges and Opportunities (http://raw.rutgers.edu/docs/wcars/8wcars/DebrecenyCAATSBanks_paper.pdf)
- Adoption of Generalized Audit Software (GAS) by External Auditors in the UK (http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.427.1261&rep=rep1&type=pdf)
Technology Use in Auditing (Source: Greenstein-Prosch et al.,2008)
- Word Processing; Computer program that facilitates entry and preparation of documents such as letters or reports.
- Electronic Spreadsheets; Software which allows the auditor to enter either alphanumeric or numeric data and manipulate it either via standard functions or auditor programmed functions
- E-Mail; Exchange of mail messages via Intranets and/or the Internet
- Electronic Working Papers; Software which generates a trial balance, lead schedules, and other schedules useful for the recording of evidence in an audit or assurance engagement
- Internet Search & Retrieval; Permits user to search text that is in electronic format and retrieve, view, and print desired text.
- Image Processing; Conversion of paper documents into electronic form through scanning and the subsequent storage and retrieval of the electronic image
- Electronic Presentations; Software that facilitates the organization and use of text, voice, and/or images to communicate concepts
- Generalized Audit Software; Computer program which helps the auditor access client computer data files, extract relevant data, and perform some audit function such as addition or comparison.
- Expert Systems; Computer software that provides relevant information and/or decision models to assist a human in making a decision or accomplishing some task.
- Embedded Audit Modules; Programmed routines incorporated into an application program which are designed to perform an audit function
- Real-time Audit Modules; Programmed routines incorporated into an application program which are designed to perform an audit function
- Database Search & Retrieval; Software that uses relational structures between data files and facilitates varying data retrieval and use.
- Simulation Software ; Abstraction of some aspect of real system via software. Auditor may use model to evaluate the reliability of information from real world sources. This may be thought of as a very high level analytical review of a company’s data.
- Flowcharting/Data Modelling; Software using the source code version of programs to produce flowcharts of program logic
- Computer Aided Systems Engineering Tools; Integrated package of computer tools that automate important aspects of the software development process to increase software development effectiveness in terms of productivity of systems development and quality of developed systems.
- Encryption Software ; Changing data using some type of encoding/decoding algorithm so that unauthorized persons who can access the encrypted data will not be able to read it or use it.
- Groupware; Software that permits auditors to categorize, store, and share data among themselves as well as communicate with each other about that data, preferably in a real-time mode.
- Cooperative Client/Server Environment; Distribution of processing functions between two or more computers as in a local area network. This also includes end-user computing where users on the network also process and store data on their personal computers.
- Workflow Technology; Software and hardware that facilitates the capture of data in the work place to improve management of the business. For example, using an electronic scanner to record the movement of materials in a warehouse based on the barcodes on the materials.
- Database Design & Installation; Software that permits the creation and use of relational structures between data files
- Time Management & Billing Systems ; Computer program, which assists in capturing, managing, billing, and reporting time, spent on professional activities.
- Test Data; A set of transactions processed by the auditor to test the programmed or procedural operations of a computer application.
- Small Business Accounting Software; Accounting software package used to record transactions, maintain general and subsidiary ledgers, and generate financial statements
- Digital Communications; Bandwidth – telecommunications devices used to facilitate the rapid and unfettered transfer of data.
- Tax Return Preparation Software; Software, perhaps incorporating expert knowledge, which assists the accountant/auditor in identifying relevant information, capturing and recording it in a manner that can be filed with tax authorities.
- Firewall Software/Hardware; Part of “security technology” that enforces an access control policy between two networks.
- User Authentication Systems; Devices used to verify that a system user is who he/she claims to be.
- EDI-Traditional; Transfer of data or payments electronically between computers using software that may, or may not, require human intervention to affect the transfer
- EDI-Web Based; The extension to XML-based EDI
- Wireless Communications; The ability to transfer digital data without the use of cables, twisted- pair, or fibre optics.
- Agent Technologies; Programmed modules that are given certain levels of authority and autonomy to act on behalf of their “supervisor”, such as to decide whether to order more inventory and from which supplier
- Intrusion Detection & Monitoring; Part of “security technology” that identifies unauthorized requests for services
- Internal Network Configurations; Linkage of individuals and data through hardware and software systems that permit the exchange of various types of data.
- External Network Configurations; Intranet, extranet, and Internet access devices than enable users physically separated from the server to access it.
- Enterprise Resource Planning; Business-wide information systems that cross boundaries
- Application Service Providers; Companies which host (provide hardware, software and connectivity) for specific business applications.